Building Phosphorus to give enterprises full visibility into their xIoT environment
Role: Director, Product Design • Industry: Network / Cybersecurity
Click for the summarized version
This case study discusses the development of the Phosphorus platform, designed to address the security challenges posed by the increasing number of insecure Internet of Things (IoT) devices within corporate networks. These devices represent significant vulnerabilities, often serving as entry points for cyberattacks.
I led the design efforts for Phosphorus, collaborated with various teams—including engineering, product management, customer success, sales engineering, and marketing—to build the platform from the ground up. The platform's core functionalities are structured around three primary themes:
- Discovery: Identifying and exposing all xIoT devices present within a target environment.
- Assessment: Providing security analysts with insights into problematic devices on their network, highlighting vulnerabilities and potential risks.
- Remediation: Equipping analysts with tools to address identified issues, such as rotating passwords or patching firmware.
A significant challenge was the need to educate organizations about the importance of securing IoT devices, as many tend to adopt a reactive approach to security. To counter this, we designed a seamless onboarding experience, enabling organizations to quickly realize the platform's value by efficiently installing agents, scanning networks and providing the contextual details around each vulnerable device.
This case study emphasizes the growing prevalence of IoT devices in corporate networks, noting that they can comprise up to 30% of such environments. Alarmingly, a significant portion of these devices are either outdated or possess known vulnerabilities, underscoring the critical need for comprehensive security solutions like Phosphorus.
The platform's success is evidenced by its adoption among Fortune 500 companies and a recent $27 million Series A2 funding round, aimed at further enhancing its capabilities to secure the expanding xIoT attack surface.
Most enterprises have three times as many embedded devices as they do people. This number will only continue to grow as IoT devices are expanding at an estimated CAGR of 31%. This presents a massive, unprotected and often undetected cyber-attack surface.
IoT is the softest target on the enterprise network with a seven-year half-life for vulnerability patching and infrequent credential rotation.
"The billions of IoT devices in use today are highly insecure and vulnerable to a wide range of attacks, which expose enterprises to many serious risks, from data breaches to ransomware,"
A Growing Problem
20% to 30% of today's corporate networks are comprised of IoT devices, with little to no security programs in place.
Across the enterprise, as high as 26% of all IoT devices are end-of-life and no longer supported with firmware updates by their manufacturer; and as many as 50% have known vulnerabilities or default passwords, with 20% of those vulnerabilities being critical CVEs (CVSS score of 9 or above). Some areas of focus include:
- Smart building and cities
- Industrial internet of things
- Enterprise IoT devices
- Network and cloud devices
- Internet of Healthcare things
- Smart ships
- Internet of Battlefield things
- Operational tech devices
Building a Solution
I joined Phosphorus as the first designer, helping to design and build the first xIoT security platform from the ground up.
Through heavy collaboration with product management, engineering, customer success, sales engineering and marketing, we were able to quickly build out a powerful platform that gave large organizations new insight into their xIoT attack surface.
Themes
Looking at the overall experience from a birds-eye view, we landed on three high-level themes for the overall customer experience:

Discover: Find and expose the devices that exist in a target environment.
Assess: Give the security analyst insight into the problematic devices on their network.
Remediate: Provide the analyst with the tools to remediate, such as rotating passwords or patching firmware.
To ensure the team always had a macro-level view of the customer experience, I mapped out an end-to-end journey, covering stages from pre-sales to product trial to retention.

This made it much easier to have conversations with the cross-functional teams as we were able to narrow in on each stage when context was needed as well as determine the touch points of engagement with the customer (support during PoV, in product support, retention strategy, etc).
Onboarding Experience

Every customer that was interested in trying out the product would go through a PoV (Proof of Value) onboarding experience to install and set up a siteManager.
Prior to adding a proper onboarding experience into the product, this process was very manual which took the time of a Sales Engineer to guide customers through the tedious process of gathering network information, spinning up an instance and installing and connecting the siteManager.
By building all of this into the product we were able to scale our PoV offering to many customers at once, allowing to free up time for our Sales Engineers.



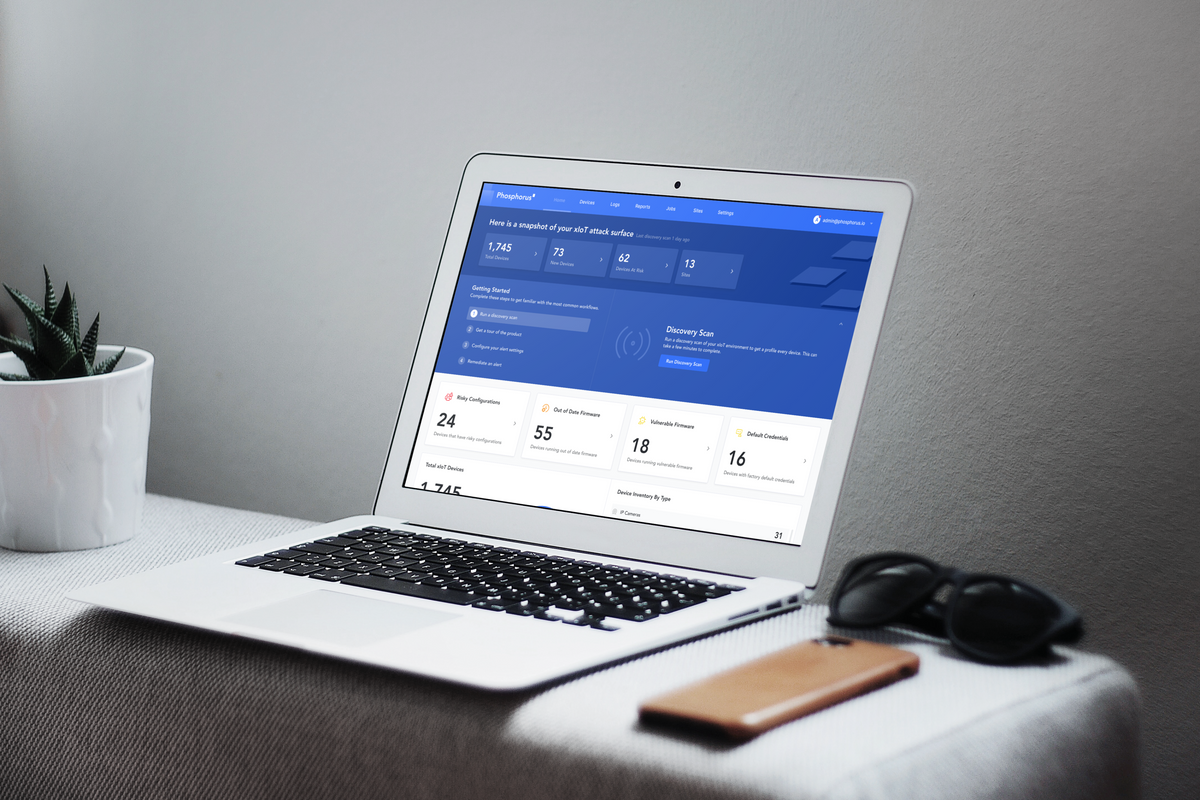
Dashboard
The dashboard is considered the starting point for the users experience with the Phosphorus platform. The main goal of the dashboard is to provide enough insight to call out things worth looking into such as alerts on devices, device inventory, remediation efforts, etc.
I went through several iterations of the dashboard and worked with the engineers on implementation which took roughly 3 weeks to build out.
The initial version was intended to evolve as we learn usage behaviors and data that's most important to analysts as they go through their workflows.




Devices
The devices page typically has the highest amount of usage and is where queries are created and saved for further investigation and reporting. The security analyst is also able to do bulk actions on a set of devices from the device list to save more time.
I went with a simple table UI to accommodate the large amount of devices with a standard faceted filter and search to build out queries.

Device Detail
Every device has a detail view that includes various data points such as the specific device detail, a health score, active alerts, device metadata, firmware version, scan and credential data.
The goal of this page was to emphasize the associated, active alerts to allow the analyst to remediate. Remediation is done by utilizing the action button which includes device-specific actions.



Sites
An organization can deploy several sites across their network so they'll need a way to manage all of their sites. The goal of this page of the platform is to:
- Give the user a quick snapshot of every sites status, whether it's ONLINE or OFFLINE.
- Provide a quick glimpse of all the devices and their health within each site.
- Call out the "Top Talkers" which are basically devices on the network that are using up the most bandwidth.

Reports
Reports provides the end user, which can be anyone from a manager to an executive, with a quick summary of their overall environment and the health across all of their xIoT devices.
The goal with the reports design is to have clear sections with data that can be actionable in the sense that data-informed remediation strategies could be done by management or the leadership team.
Providing a way to generate a report for a specified period of time satisfies a few goals from both a business and customer perspective:
- Management can leverage reports to exemplify the value that they're getting from using the platform to their executive leadership team.
- Leadership can get a quick overview of their xIoT environment and make informed decisions on how they'll orchestrate their security measures and investments.
- Management is able to make informed decisions on how they'll remediate issues that they find and track them over time.

Changelog
A simple changelog page to inform customers of the latest Phosphorus feature releases, product enhancements, design updates and important bug fixes.

Multi-Tenancy
Being able to support multiple tenants is on the mid-term roadmap. In order to get ahead and align with the team on what that means in the product, I tend to kick off these kind of projects with a collaboration session with the cross-functional teams.
The outcome is team alignment and an artifact that we can refer to once the UI design phase kicks off.

Design System
I built out a rudimentary design system (Mineral) in parallel to designing the product in order to maintain everything from iconography, fonts, colors and UI components. This speed up the process a bit and allowed me to globally update components or elements in one place which populated across the project branches.

The long-term goal was to eventually bring on a FT designer to extend and maintain this and move it over to Storybook, but given the speed of every project and limited resources, a Figma design system in the short term should suffice.






Process & Dev-Cycle Workflows
Aside from the actual work of building out the product, I'd be remiss to not touch a bit on some of the operational aspects.
Early on when working with cross-functional teams I find it makes my life easier to get alignment (and buy in!) on how we'd all work together. Laying out a workflow in a visual such as this helped me work with product management and engineering on structuring a starting point for how we'd operate. The goals was to then dive into each block and determine what sort of activities would work for our team and culture.
As with building product, how teams work together is an iterative activity and will always need to evolve accordingly as you add more people to the team or the product splits into a portfolio of multiple offerings.
That said, this workflow is flexible in the sense that it's not a rigid checkbox of things we have to do without any sort of intention.


Outcome
The Phosphorus platform is always being improved based on the continuous feedback cycle we've created with our customers. When feedback, new customer insight or bugs come in, I'm usually one of the first to hear about it so I'll spin up a ticket in Jira and work with the engineering manager to get resources on the fix.
To date, the efforts have resulted in helping a growing list of fortune 500 customers harden their xIoT attack surface and raising a series A of $38 million.

Comments ()